Replacing the Pure Storage FlashArray VASA Certificate
Maintaining Certificates in your environments is an important thing to do to make connections between your client and server are encrypted. With this blog we will go over how to replace your Pure Storage FlashArray Certificate for the vStorage APIs for Storage Awareness (VASA) using a Microsoft Certificate Authority.
Previously, we covered how to replace the FlashArray Management Certificate now we will show how to replace the VASA one. With the VASA certificate there are a few reasons we may want to replace it with a signed certificate one being encryption, but the other is it will allow you to register a storage provider with multiple vCenter Servers for vVols.
Checking Certificate Status
The VASA Certificate can only be replaced via the CLI. If we run *purecert list we can see the current status of our array certificates.
pureuser@david-fa1> purecert list
Name Status Key Size Issued To Issued By Valid From Valid To Country State/Province Locality Organization Organizational Unit Email Common Name
management imported 2048 david-fa1.newstack.local newstack-DC01-CA 2020-03-30 13:38:49 PDT 2022-03-30 13:38:49 PDT US CA MTV Pure Storage, Inc. Pure Storage, Inc. [email protected] david-fa1.newstack.local
vasa-ct0 imported 2048 10.21.230.44 CA 2020-03-08 08:11:26 PDT 2021-03-09 07:11:26 PST US - - Pure Storage Pure Storage - 10.21.230.44
We can see that our management certificate has already been replaced by our CA, we will proceed to replace our vasa-ct0 certificate.
In this blog this is a non-production FlashArray with a single controller. In a production environment this will be repeated for vasa-ct0 and vasa-ct1
Construct Certificate Signing Request
Unlike the management certificate, the vasa certificate is only an IP based name, there is no need to add in any FQDN for the array.
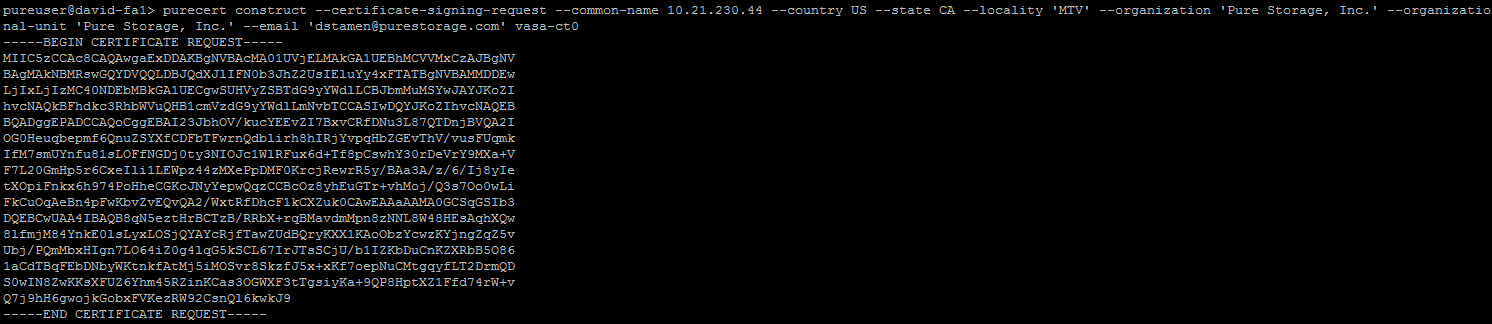
Let’s create a CSR for vasa-ct0 using the following command.
purecert construct --certificate-signing-request --common-name 10.21.230.44 --country US --state CA --locality 'MTV' --organization 'Pure Storage, Inc.' --organizational-unit 'Pure Storage, Inc.' --email '[email protected]' vasa-ct0
Request a Certificate Using the CSR from Microsoft Certificate Authority
With our CSR in hand we can navigate to our Certificate Authority to request a certificate. You can access the certificate request UI usually by navigating to https://FQDN/certsrv
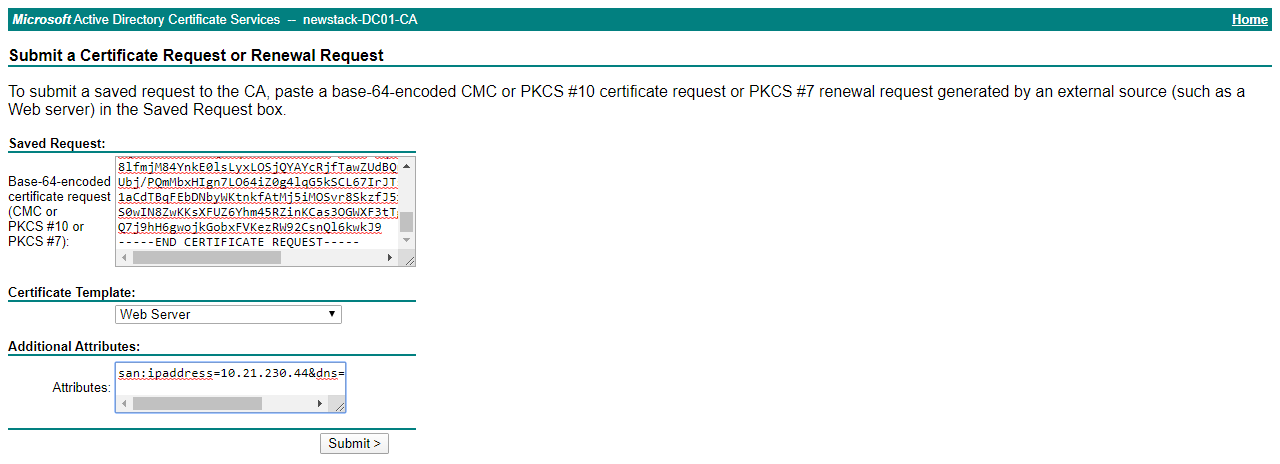
We will click on Request a certificate and then advanced certificate request. As mentioned earlier, the SAN will not contain Common Name but with the Certificate Request we can easily add in the Additional Attributes to include it:
san:ipaddress=10.21.230.44&dns=10.21.230.44
Click on Submit and download the certificate as Base 64 encoded
Replacing the Management Certificate
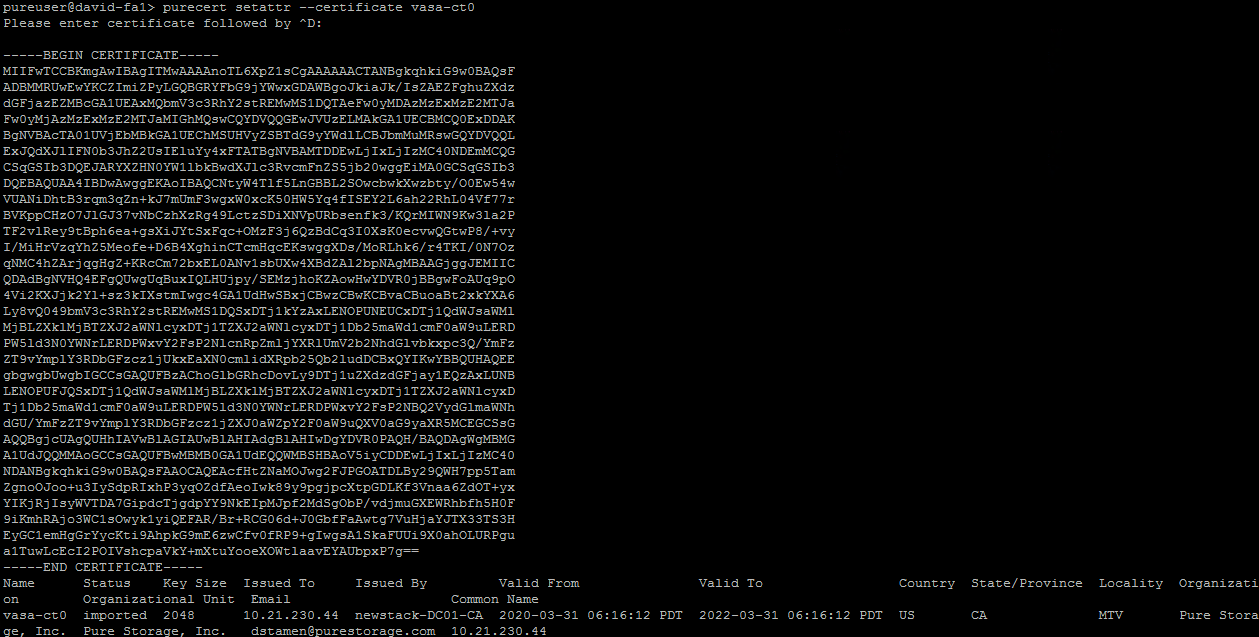
Once you have your certificate you can navigate back to the CLI and run purecert setattr –certificate vasa-ct0 to replace the certificate.
"^D" is equivalent to “Ctrl+D”
Now if we rerun purecert list we can see our vasa-ct0 certificate is now updated.
pureuser@david-fa1> purecert list
Name Status Key Size Issued To Issued By Valid From Valid To Country State/Province Locality Organization Organizational Unit Email Common Name
management imported 2048 david-fa1.newstack.local newstack-DC01-CA 2020-03-30 13:38:49 PDT 2022-03-30 13:38:49 PDT US CA MTV Pure Storage, Inc. Pure Storage, Inc. [email protected] david-fa1.newstack.local
vasa-ct0 imported 2048 10.21.230.44 newstack-DC01-CA 2020-03-31 06:16:12 PDT 2022-03-31 06:16:12 PDT US CA MTV Pure Storage, Inc. Pure Storage, Inc. [email protected] 10.21.230.44
Conclusion
Replacing certificates is always a great idea! If you have not replaced your management certificate now is a great time.
comments powered by Disqus